Today, We want to share with you Functions of a DBMS – Database Management System.In this post we will show you disadvantages of database management system & components of database management system, hear for what are the main components of a database system? we will give you demo and example for implement.In this post, we will learn about Functions of a Database Management System with an example.
Functions of a DBMS – Database Management System
There are the Following The simple About database management software definition Full Information With Example and source code.
As I will cover this Post with live Working example to develop main components of a database, so the some major files and Directory structures for this example is following below disadvantages of database management system.
What is a Database?
A database is a group of related information which represents particular aspect of the real world. A collection of data(Database) structure is designed to be built as well as populated with information for a certain task with functions of database administrator.
What is DBMS?
definition database management system
Database Management System (DBMS) is a software for storing as well as retrieving customers’ information with define database management system while considering appropriate security measures. It consists of a group of programs which manipulate the DB. The DBMS accepts the request for information from an application as well as instructs the operating structure to provide the specific information. In large structures, a DBMS helps customers as well as other third-party software to store as well as retrieve information is a data management system definition.
determining databases and data communications, rdbms wikipedia
Popular DBMS Software & Functions of a DBMS
Here uses of database software, is the list of particular popular DBMS structure: define database software
- MySQL
- Microsoft Access
- Oracle
- PostgreSQL
- dBASE
- FoxPro
- SQLite
- IBM DB2
- LibreOffice Base
- MariaDB
- Microsoft SQL Server etc.
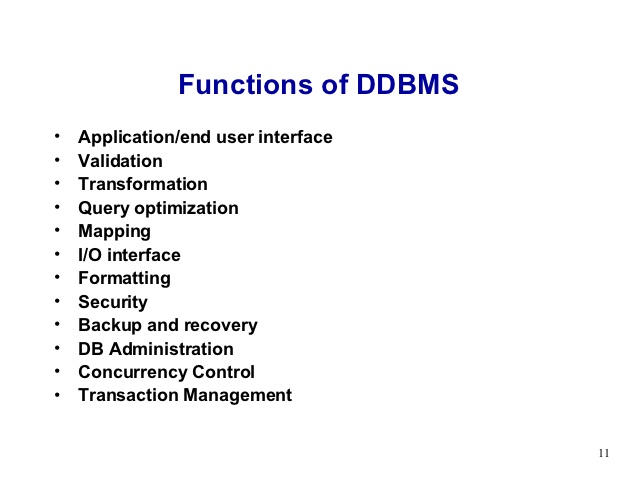
There are several functions that a DBMS executes to ensure information integrity as well as consistency of information in the collection of data. The ten functions in the DBMS are: information dictionary management, information storage management, information transformation as well as presentation, security management, multicustomer access control, backup as well as recovery management, information integrity management, collection of data access languages as well as application programming interfaces, collection of data communication interfaces, as well as transaction management.
Functions of a DBMS
So, what does a DBMS really do? It organizes your files to give you more control over your information with features of database management system.
A DBMS creates it possible for customers to create, edit as well as update information in collection of data files. Once created, the DBMS creates it possible to store as well as retrieve information from those collection of data files.
All the available Functions of a DBMS
More specifically, a DBMS provides the following functions:
- Concurrency: concurrent access (meaning ‘at the same time’) to the same collection of data by multiple customers
- Security: security rules to dephaseine access rights of customers
- Backup & recovery: processes to back-up the information regularly as well as recover information if a problem occurs
- Integrity: collection of data structure as well as rules improve the principle of the information
- Data descriptions: a information dictionary provides a description of the information
Within an organization, the development of the collection of data is typically controlled by collection of data administrators (DBAs) as well as other specialists. This ensures the collection of data structure is efficient as well as reliable.
Database administrators also control access as well as security aspects. For sample, different people within an organization use databases in different ways. Some employees may simply want to view the information as well as perform basic analysis. Other employees are actively involved in adding information to the informationbase or updating existing information. This means that the collection of data administrator required to set the customer create database permission denied in database master. here we did not any particular one who only requireds to view the collection of data to accidentally remove parts of the group of more data.
DBMS executes main important functions that 100% sure the principle as well as consistency of the information in the collection of data. The most important functions of collection of data Management System are
Functions of a DBMS
- Data Dictionary Management
- Data Storage Management
- Data Transformation & Presentation
- Security Management
- Multi customer Access Control
- Backup & Recovery Management
- Data Integrity Management
- Database Access Languages & Application Programming Interfaces
- Database Communication interfaces
functions of database management system
here learn about to you database management software examples with Functions of a DBMS.
1.Data Dictionary Management
Data Dictionary is where the DBMS stores definitions of the information elements as well as their relationships (metadata). The DBMS uses this function to look up the required information component structures as well as relationships. When programs access information in a collection of data they are basically going through the DBMS. This function removes structural as well as information dependency as well as provides the customer with information abstraction. In turn, this creates things a lot easier on the end customer. The Data Dictionary is often hidden from the customer as well as is used by Database Administrators as well as Programmers.
2.Data Storage Management
This particular function is used for the storage of information as well as any related information entry forms or screen definitions, report definitions, information validation rules, procedural code, as well as structures that can handle video as well as picture formats. Users do not need to know how information is stored or manipulated. Also involved with this structure is a phase called performance tuning that relates to a database’s efficiency in relation to storage as well as access speed.
3.Data Transformation as well as Presentation
This function exists to transform any information entered into required information structures. By using the information transformation as well as presentation function the database management system can dephaseine the difference between logical as well as physical information formats.
4.Security Management
This is Very smart or great IMP functions/Methods in the database management system. Security management sets rules that dephaseine specific customers that are authorizeed to access the collection of data. Users are given a customername as well as password or particulartimes through biometric authentication (such as a fingerprint or retina scan) but these types of authentication tend to be more costly. This function also sets restraints on what specific information any customer can see or manage.
5.Multicustomer Access Control
Data integrity as well as information consistency are the basis of this function. Multicustomer access control is a very useful tool in a database management system, it enables multiple customers to access the collection of data simultaneously without affecting the integrity of the collection of data.
6.Backup & Recovery Management
Backup as well as recovery is brought to mind whenever there is potential outside threats to a collection of data. For sample if there is a power outage, recovery management is how long it takes to recover the collection of data after the outage. Backup management mention to the information safety as well as integrity; for sample backing up all your mp3 files on a disk.
7.Data Integrity Management
The database management system enforces these rules to reduce things such as information redundancy, which is when information is stored in more than one place unnecessarily, as well as maximizing information consistency, making sure collection of data is returning correct/same answer each time for same question asked.
8.Database Access Languages & Application Programming Interfaces
A query language is a nonprocedural language. An sample postgres drop database of this is SQL (structured query language). SQL is the most common query language supported by the majority of database management system vendors. The use of this language creates it easy for customer to specify what they want done without the headache of explaining how to specifically do it.
9.Database Communication Interfaces
This mention to how a database management system can accept different end customer requests through different network environments. An sample of this can be easily related to the internet. A database management system can provide access to the collection of data using the Internet through Web Browsers (Mozilla Firefox, Internet Explorer, Netscape).
10.Transaction Management
This mention to how a database management system must supply a method that will guarantee that all the updates in a given transaction are made or not made.All transactions must follow what is called the ACID properties.
Database Management Using SQL
This chapter discusses nine functions of collection of data structures. The objectives
important to this chapter are:
- Understanding functions & services
- Update & retrieval
- Catalog features
- Concurrent update
- Data recovery
- Security services
- Data integrity
- Data independence
- Replication
- Utility services
All the Examples of what is sql plus?, sql unique count, sql trigger, rdbms sql, use distinct in sql, sql server while loop, sql server reporting tool, sql objective questions and answers, difference between sql and plsql, sql server while loop, object_id sql, sql server load balancing or many more
Concepts:
This chapter discusses particular necessary as well as particular desirable features to
look for in a DBMS. Each should be implemented as an available service
in the DBMS, even if you have no need for all of them.
Update as well as retrieval are necessary features. A structure that does
not authorize you to change, add, or delete information would not be useful. upgrade
more addeds the ability to change, add, as well as delete records.
Catalog services are used to describe a DBMS. A catalog would
more added descriptions of all tables, of the relations between them, of
the information types used in the tables, as well as of the constraints used for each
field. Some structures refer to this kind of reference as a information dictionary.
The text mention to the concept as metadata about the DBMS.
Concurrent upgrade problems occur when multiple customers input information
into Database tables in a way that causes the loss of particular of that information.
A phase used here is transaction, which is defined as the steps
needed to complete a single task. Some classic scenarios are offered for
overcoming this problem:
- batch processing – have all the Based on atransactions saved in a
queue application, then some processed in step by step next to the second one turn by an upgrade program. The
text represent a structure that may save the transactions as well as process all
upgrades once a day. This would be fine, as long as the next customer did
not need to know the effects of the last customer’s upgrades. A structure that
provides real time access to inventory information, or one that executes registrations
for classes are samples of structures that cannot wait very long for the
upgrade process to run. - locking – a DBMS may authorize for secureing single or multiple
rows in a Database table, or it may authorize for secureing entire tables.
Data is locked so that other customers cannot access that information until it
is unlocked. This provides for a clean environment in which you are
not authorizeed to access information until you have the freedom to change it.
The text represent a two-phase access to secureing. The begining phase
is the growing phase, in which secures are registered to as many rows
or tables as necessary to accomplish the customer’s transaction uninterrupted.
The second phase is the main of the shrinking phase, in which secures are free
as the changes are finished as well as the secures are no longer needed. - timestamping – here access assigns a time to each request,
as well as it processes them in chronological order. This is such as a mass processing,
in that an order of events is assigned, but unlike it in that we do
not wait an arbitrary time for the processing.
A problem that occurs with concurrent update is called deadlock
or deadly embrace. Two customers can start transactions that cannot
be completed unless they get access to information that the other customer has
already
locked. In the worst case, the information that We have locked cannot be unlocked
until the lock that you have registered is free. If you as well as We are in
the same status, we are deadlocked. A deadlock is resolved by having
the database management system designate one of us as the Like same a victim, backing out of that
transaction, rescheduling it, as well as performing the other one. This should
authorize both
transactions to be performed, but one is forced to happen later than
the other.
Data recovery is necessary on any computer structure that saves important
information. A database management system structure may use standard reserve tape structures, but it may have
particular additional features. Journaling authorizes the structure to make a record
of transactions, a all the system log storege file that can be used in case a all the Data as a restoration is
necessary. The main idea is leads to a couple of cases:
- forward recovery – Like as a there is a setback generateing
us to re-establish the database management system to the phase is was in N(Like as one two or threee) days ago, as that
is the date of our last reliable reserve. This
recovery will then authorize us to activity the account of transactions
to bring the database management system back to the present. Obviously, here requires that
accounts be kept around for particular time to make here possible. - backward recovery – also called rollback, here is the
activity of backing away from an error condition by restoring the structureto an earlier phase. We can do here by simply performing a re-establish all the data,
or by failure the transactions in a account in reverse order.
Security services are common on most computer structures. Three common features
are described:
- encryption – storing as well as transmitting documents folders and files in an encrypted
mode therefor that they are not readable unless you are running the database management system - authentication – authentication typically involves a customer ID
as well as a password to gain access to the structure. Biometric authentication
is used in particular structures, which may require a fingerprint or other physical
ID in addition to an ID as well as password. - authorization – authorization is the granting of rights to
parts of the structure to particular customers. here can more added authorizeing groups
of customers to see only parts of the collection of data (views).
Integrity Advantages more added the constraints that authorize only specific
kinds of information to be entered in specific fields. Constraints can restrict
the type of information entered in a field, the range of acceptable values, as well as
the format of the information.
A DBMS should support information independence in that it should authorize
for changes to the information as well as changes to the tables without having to rebuild
the entire structure. Change samples listed more added changing the length
of a field, adding fields, as well as creating indexes.
Data replication is the process of keeping multiple copies of the
collection of data in multiple places. This may be done for fault tolerance or it
may be done to make the information more accessible to customers in distant locations.
Multiple copies of the information require methods to synchronize the copies.
Updates may be authorizeed in one or more copies, but all changes must be
propagated to all other copies.
Utility services are services to authorize you to perform actions
associated with the operating structure in use, like file copying, running
other programs, as well as writing as well as running script files.
Web Programming Tutorials Example with Demo
Read :
Summary
You can also read about AngularJS, ASP.NET, VueJs, PHP.
I hope you get an idea about common database software.
I would like to have feedback on my infinityknow.com blog.
Your valuable feedback, question, or comments about this article are always welcome.
If you enjoyed and liked this post, don’t forget to share.